Zero-Knowledge Proofs Explained: Privacy in Web3 (Beginner’s Guide)
.webp)
tl;dr
- Zero-knowledge proofs let someone prove they know a secret without revealing the secret itself.
- They are useful whenever privacy and trust are both important.
- ZKPs are transforming Web3 privacy by allowing verification without exposing wallet balances, transaction details, or identity.
- ZKPs are transforming Web3 privacy by allowing verification without exposing wallet balances, transaction details, or identity.
- Main types beginners should know: ZK-SNARKs, ZK-STARKs, Bulletproofs, and emerging protocols like PLONK, each with different strengths and applications.
What Are Zero-Knowledge Proofs? A Simple Explanation
Zero-knowledge proofs (ZKPs or ZK-Proofs) are clever cryptographic techniques that let someone prove they know a piece of information, like a password or a solution. They do this without ever revealing what that information actually is. It’s the digital equivalent of saying, “I know a secret, and I can prove it to you without telling you the secret.”
This makes ZKPs incredibly powerful for situations where privacy and trust both matter.
How Do Zero-Knowledge Proofs Work? (Real-Life Examples)
In a typical zero-knowledge interaction, there are two parties. The prover is the one who claims to know a hidden piece of information, like a password or a solution to a puzzle. The verifier is the one who needs to be convinced that the prover really does know it, while learning nothing about the secret itself. Through a series of carefully designed mathematical steps, the prover demonstrates knowledge, and the verifier checks the logic.
At no moment is the secret exposed.
ZK-Proofs Analogies
In the “Where’s Waldo?” example, you claim you know where Waldo is in a huge puzzle. To prove it without giving away his location, you place an opaque sheet with a Waldo-sized hole over the page. Your friend sees Waldo through the hole but nothing else, so they know you found him while learning nothing about the puzzle. Repeating the test makes it clear you didn’t just guess.
The second analogy uses a color-blind friend and two cards, one red, one green. Your friend can’t see the difference, but they can still test your claim. They hide the cards behind their back, reveal one at random, and you correctly identify it repeatedly. You’ve proven the cards differ without revealing anything about the actual colors.
This is the heart of zero-knowledge.
Why ZK-Proofs Are a Game-Changer for Web3 Privacy
Zero-knowledge proofs solve the biggest dilemma in blockchain: how to keep systems open and verifiable without exposing every detail of a user’s financial life. On blockchains like Bitcoin or Ethereum, transparency often turns into surveillance, anyone can see your wallet balances, transaction history, and counterparties.
ZK-proofs flip this dynamic by allowing the network to verify that something is true without revealing the data behind it.
This shift starts with the core idea: “verify, don’t reveal.” Just like proving you found Waldo without showing his location, ZK-proofs let users prove ownership, eligibility, or balances while keeping the underlying information hidden.Transactions can be validated without exposing who sent what to whom. Identity checks can confirm age or nationality without sharing documents. Even large traders can operate privately without being front-run by bots.
In short, this shifts Web3 from a "Don't be evil" model (hoping companies don't misuse your data) to a "Can't be evil" model.
The Main Types of ZK-Proofs Every Beginner Should Know
There are three main types of zero-knowledge proofs that beginners should know: ZK-SNARKs, ZK-STARKs, and Bulletproofs (as well as other emerging protocols like PLONK). Each has different strengths and uses.
ZK-SNARKs
ZK-SNARKs, short for “Succinct Non-Interactive Argument of Knowledge,” are one of the most widely used zero-knowledge systems today. They produce extremely small proofs that can be verified very quickly, making them ideal for blockchain environments where efficiency is critical.
The main drawback is that they require a trusted setup, a one-time ceremony that must be performed honestly to maintain security.
Despite this tradeoff, ZK-SNARKs power major privacy technologies, most famously Zcash, and are heavily used in Ethereum Layer 2 rollups and privately.
ZK-STARKs
ZK-STARKs, which stand for “Scalable Transparent ARguments of Knowledge,” remove the trusted setup completely. Their transparency improves trust and security, and they scale exceptionally well, handling much larger computations than SNARKs. Although STARK proofs are larger in size, they offer benefits like easier verification, simpler design assumptions, and strong quantum resistance.
This makes them increasingly popular in next-generation blockchain systems focused on long-term security and massive throughput.
Bulletproofs, PLONK, and Other Systems
Other zero-knowledge systems fill important niches. Bulletproofs are compact, efficient, and don’t rely on a trusted setup, making them ideal for confidential transactions in various cryptocurrencies.
PLONK is a flexible, universal proving system designed for broad usability, enabling developers to reuse the same setup across many applications. Additional systems, such as Groth16, Sonic, and Marlin, each optimize for different goals like proof size, speed, or developer friendliness.
Top Real-World Use Cases of Zero-Knowledge Proofs in 2026
Zero-knowledge proofs are now powering privacy, scalability, and trust across blockchain and Web3 in 2026. Here are top real-world use cases:
Private Transactions
Zero-knowledge proofs are powering confidential payments and private DeFi interactions. Zcash and Horizen use zk-SNARKs to hide sender, receiver, and transaction amounts on public blockchains. Aztec Network enables private DeFi on Ethereum, allowing users to trade or interact with protocols like Uniswap without exposing transaction details. Secret Network leverages ZKPs for encrypted smart contracts, supporting private apps and confidential transactions across decentralized platforms.
Scalable Layer-2 Rollups
Layer-2 rollups like zkSync, StarkNet, Polygon zkEVM, and Scroll use ZKPs to boost Ethereum’s speed, lower costs, and enhance privacy. By batching transactions off-chain and proving their correctness with ZK-SNARKs or ZK-STARKs, these rollups settle efficiently on-chain. The result is thousands of transactions per second, lower fees, and a more scalable, private blockchain experience.
Identity & Credential Verification
ZKPs let users prove attributes like age, citizenship, or KYC compliance without revealing sensitive personal data. This enables on-chain passports, selective compliance checks, and confidential access in DeFi. For instance, ING Bank uses ZKPs to confirm mortgage eligibility without exposing financial details, protecting both users and institutions.
Private Voting & Confidential DeFi
DAOs and governance platforms employ ZKPs for verifiable, private voting. DeFi protocols use ZKPs for confidential lending, trading, and stablecoins, ensuring activities are provable without public exposure.
Other Emerging Use Cases
ZKPs also enhance supply chain transparency, regulatory audits, and secure data sharing in healthcare and enterprise, verifying authenticity or compliance without exposing proprietary information.
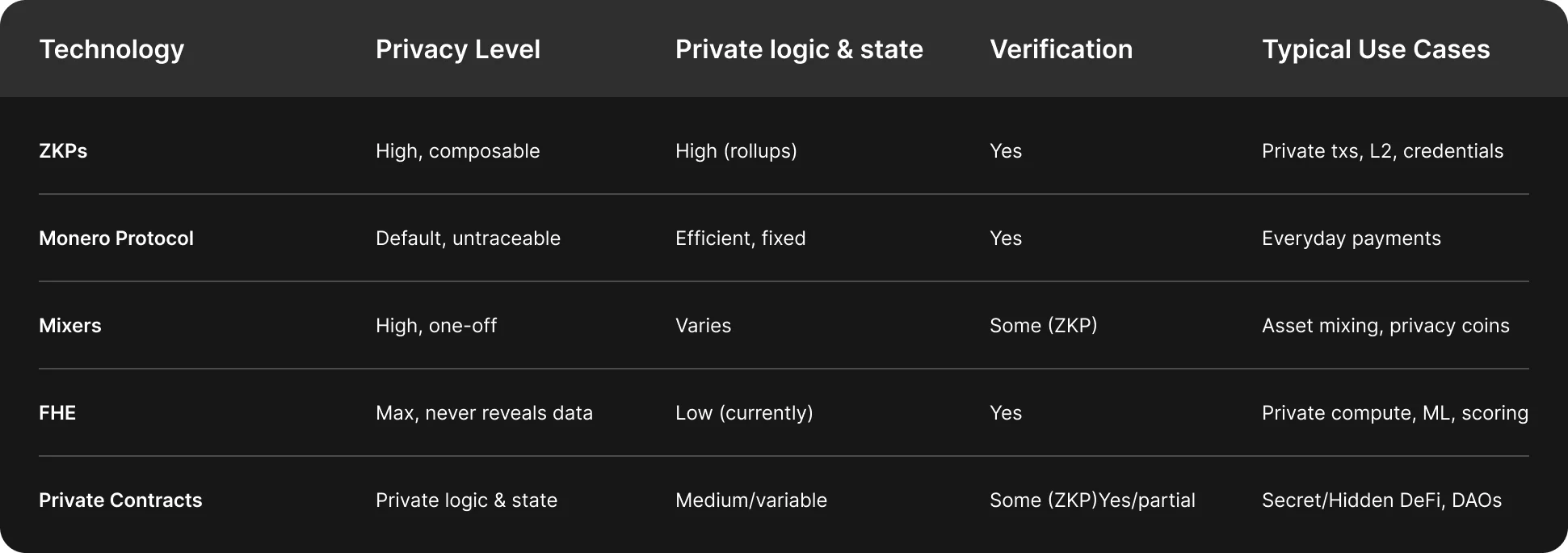
Zero-Knowledge Proofs vs Other Web3 Encryption Types
ZK-proofs, Monero's protocol-level encryption, mixers, fully homomorphic encryption (FHE), and private smart contracts, approach on-chain privacy and verification with fundamentally distinct cryptographic strategies.
Zero-Knowledge Proofs (ZKPs)
ZKPs, including zk-SNARKs and zk-STARKs, let users prove knowledge of a secret or the validity of a transaction without revealing sensitive details. They are widely used in Zcash, Ethereum Layer 2 rollups, and Aztec to enable private transfers, scalable batch verification, and composable privacy-preserving smart contracts. ZKPs are concise, fast to verify, and increasingly universal.
Monero’s Protocol-Level Encryption
Monero achieves privacy by default using a multilayered approach: ring signatures hide the sender among decoys, stealth addresses obscure recipients, and Ring Confidential Transactions (RingCT) conceal amounts. Bulletproofs provide compact zero-knowledge range proofs to make RingCT scalable. Unlike ZKPs, Monero relies on these cryptographic techniques at the protocol level, offering private, unlinkable transactions for all users without optional proofs.
Mixers (e.g., Tornado Cash)
Mixers anonymize transactions by pooling deposits and withdrawals, making it difficult to trace inputs to outputs. Some, like Tornado Cash, leverage zk-SNARKs to allow private withdrawals while proving legitimacy. Mixers are effective for one-off privacy but rely heavily on user activity and pool size for strong anonymity.
Fully Homomorphic Encryption (FHE)
FHE enables computation directly on encrypted data, returning results only to authorized parties. This allows private smart contracts or outsourced computations without exposing input data. FHE offers strong privacy but is computationally heavier than ZKPs, making it less practical for on-chain verification today.
Private Smart Contracts (e.g., Secret Network)
These contracts execute encrypted logic and state, revealing outputs only to authorized users. They combine symmetric encryption, TEEs, and sometimes ZKPs for verifiability. This enables private DeFi, cross-chain privacy, and confidential governance, expanding privacy beyond transactions.
Advantages and Limitations of Zero-Knowledge Proofs
Zero-knowledge proofs offer unmatched privacy by allowing users to prove knowledge or transaction validity without revealing any sensitive information. They enable scalable blockchain solutions by supporting batch verification, private transactions, and composable smart contracts. This combination of privacy and efficiency makes ZKPs a cornerstone for modern Web3 applications, from private DeFi to Layer-2 rollups.
However, ZKPs come with limitations. Generating proofs can be computationally intensive, requiring significant processing power, especially for large or complex computations. Additionally, their mathematical complexity makes auditing and implementation challenging, demanding careful review and expertise to ensure security.
Despite these hurdles, ongoing research is steadily improving efficiency and usability across blockchain ecosystems.
Frequently Asked Questions About Zero-Knowledge Proofs
Are zero-knowledge proofs 100% secure?
No system is perfectly secure. Well-designed ZKPs like zk-SNARKs and zk-STARKs are highly secure, but risks exist from software bugs, side-channel attacks, or trusted setup procedures in some cases.
Do zero-knowledge proofs slow down blockchain transactions?
Proof generation can be computationally intensive, but verification is fast. In Layer-2 rollups, ZKPs enable batch processing, improving scalability and throughput.
Which cryptocurrencies use zero-knowledge proofs?
Zcash, Ethereum Layer-2s (zkSync, StarkNet, Polygon zkEVM), Aztec Network, and Secret Network use ZKPs for privacy and scaling.
What’s the difference between ZK-SNARKs and ZK-STARKs?
ZK-SNARKs require a trusted setup and have smaller proofs; ZK-STARKs are transparent, quantum-resistant, and highly scalable.
Will Ethereum fully switch to zero-knowledge rollups?
Ethereum is adopting zk-rollups to scale and enhance privacy, but they complement rather than replace the base layer.



%20Payments.webp)